Share this
By Dr Hayleigh Bosher & Samuel West
02 Mar 2020
Dr Hayleigh Bosher is Lecturer in Intellectual Property Law at Brunel University London. Samuel West is a Security Engineer for Libraesva
The Coronavirus has received extensive media attention, much of which has been seen to strike fear and panic. Now hackers, spammers and fraudsters have used this as an opportunity to launch new attacks. This article explains a real-life attack to show how and why they work, what to look out for and what can be done to stop the hackers.
Libraesva, a UK and Italy based Security Software Vendor, recently discovered targeted phishing and whaling campaigns based around the Coronavirus outbreak. Phishing is the fraudulent practice of sending emails pretending to be from recognisable companies in order to get individuals to reveal personal information such as passwords or credit card numbers and siphon funds from the organisation. Whaling is a specific type of phishing attack that targets high-profile employees, such as the CEO or CFO.
The image below shows a real example of a whaling email received and blocked by Libraesva. The email shows how the attackers pretended to be the director of Milan University, warning internal users of the outbreak of Coronavirus and what steps to take to prevent further spread. In this case, the hacker was able to change the code of the email to make it appear to be sent from a trusted sender – the Director of the University. Unlike a typical whaling attack that immediately asks for transfer or funds, this hacker, taking advantage of the fear around Coronavirus, asks readers to download a guide to stop the disease.
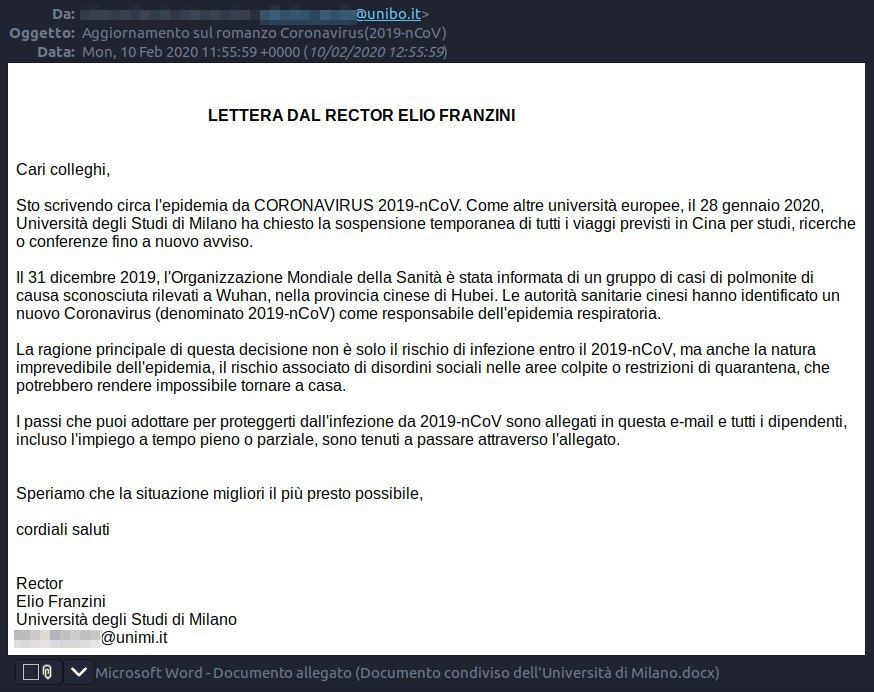
Email Spoof of director of Milan University, sent from a University of Bologna compromised account
The interesting thing about this attack is that the underlying sender of the email is trusted by the University, gaining the trust of the receiving email server technology. The email states, on many occasions, the dangers of the virus 2019-nCoV as a respiratory epidemic, and makes a call to action for readers to quickly look at the attached document which is a simple docx file with a link. However, once a reader clicks to access the document, the hacker has set up a fake Office 365 login page shown in the image below - which requires users login and passwords to see the document.
Once ‘Download File’ is selected the motivation of the hacker and the scam becomes clear, asking for University user login details and passwords.

The landing page when following the link from the attached document.
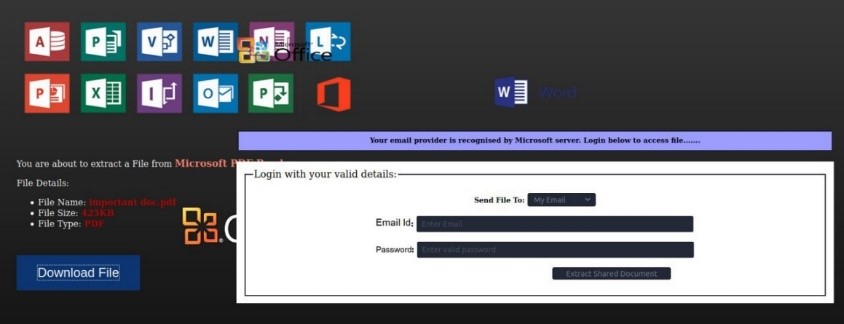
After selecting download file, we can clearly see credential harvesting fields.
The risks are very high, hackers can sell the credentials that they obtain, or use them to ex-filtrate even more data. They could also log in as a staff member and use that to send further malicious emails, which is how this email was able to be sent in the first place.
But isn’t this illegal?
Yes, of course, this type of activity is illegal. Most countries around the world have laws against this type of cybercrime. In the EU there is the convention of Cybercrime and in the UK we have the Computer Misuse Act. These regulations make it illegal to interfere with the functioning of a computer. There are also laws against fraud and the GDPR which protects data and this would come into play because of the data the hackers illegally obtained.
The problem is that these hackers are difficult to locate, as they often use technological measures to ensure that they are not traceable.
What else can we do about it?
This example was located and prevented through Libraesva’s email security software and management. It was observed that the spoofed sender of the email was on a compromise protection list known in the industry as “BEC – Business Email Compromise”, so additional checks were undertaken.
The email was sent using an email address of another University, after that person was successfully hacked. Using Libraesva’s Adaptive Trust Engine’s relationship monitoring, we saw that the trust between these two Universities was quite high. But the trust between the two individual users was low, we didn’t let the organisational trust get in the way of understanding the true nature of the email.
The third indicator was that the email came externally to the Milan University users, which doesn’t make any sense, all emails from the director will 99% of the time come via the internal route, meaning this is obviously fake.
The coronavirus is an opportunity for hackers to take advantage of the fear to scam people, business and universities. It is important to be aware of these risks and take the necessary precautionary action.
Using the above indicators, Libraesva has built a dedicated technology to halt these kinds of attacks, make sure your IT team employ some Email Security, as this is the main way threats and malicious activity can get into your organisation.